
You can centralize batch monitoring of resources, leaving the inefficient perspective of single-instance, single-resource management, and making operational monitoring more efficient and orderly.

Provides you with a wealth of monitoring indicators and alarm indicators, you can know the status of resources at any time.

Using efficient time series data storage can save storage space and improve query performance.

Provides you with metrics of common infrastructure level virtual resources, including but not limited to cloud host CPU, memory and other metrics. You can uniformly view the running status of various IAAS resources.

The alarm strategy of the cloud host monitoring item can be customized, and the alarm information can be pushed by email, which is convenient for you to know the health status of the cloud host in time.

Collects and persists critical state change events and user login audit logs generated by IaaS layer resources, and provides report export functions.

Using the characteristics of increasing time, repeated dimensions and smooth changes of indicators, it can reasonably choose coding compression algorithms to improve data compression ratio, and save storage space for you by pre-reducing accuracy and aggregating historical data.

If your cluster supports multiple zones, the service supports centralized presentation of monitoring and alarm data of cloud hosts in all zones in a unified interface.

By monitoring the CPU usage, memory usage, disk and other basic indicators of the cloud host, to ensure the normal running state of the cloud host, avoid the scenario that the business can not run normally because of the excessive use of resources.
Monitor the top 5 vCPU and memory usage of the whole platform to let the operation and maintenance know the load of the cloud host.
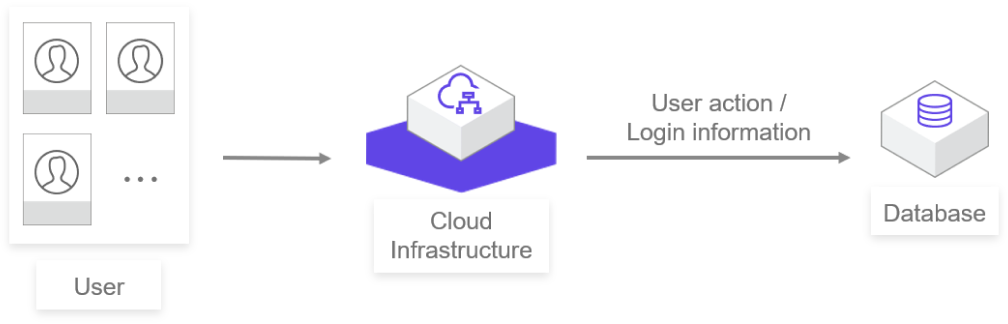
The log of user's operation/login information is collected to facilitate the user to view the system operation and locate the problem.
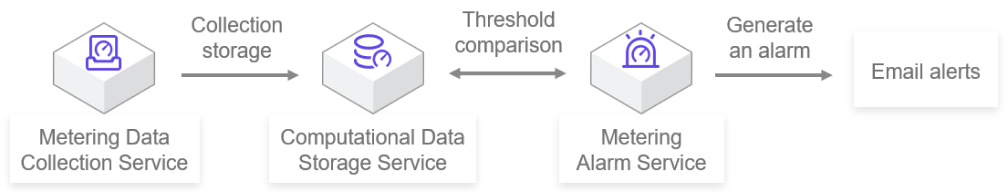
According to the alarm rules you create, when the monitoring indicators for the cloud host exceed the set threshold, an alarm message can be sent, so that you can obtain an anomaly notification in time and deal with the alarm cloud host in time.
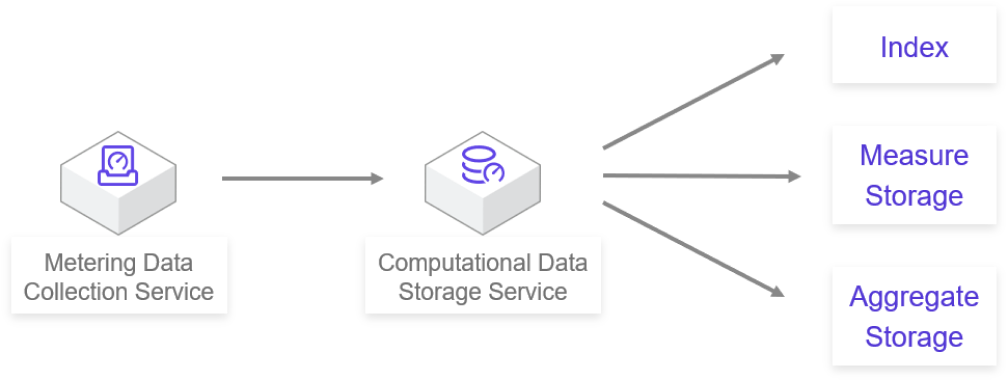
It aims at the aggregation and storage of ultra-large scale measurement data, and provides users with access to measurement and resource information at the same time.