
Private CA, certificate and key are generated by domestic cryptographic algorithm.

It can be integrated with identity and access management, computing services, mirror services, and exclusive load balancing services to provide certificate and key services for cloud products.

Provides certificate and key lifecycle security management, combined with strict access control, to ensure that the certificate and key are safe and reasonable use.
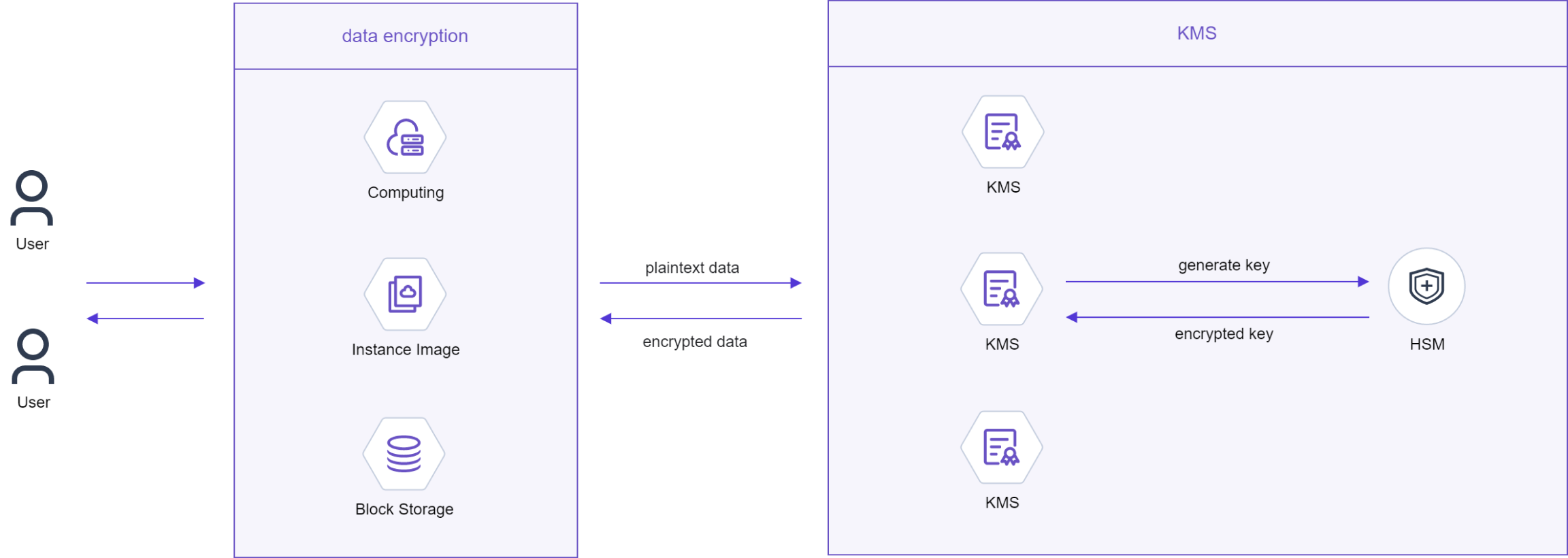
When a user creates a resource using a cloud service, the resource containing sensitive information can be encrypted by the key provided by the key service. The key is generated by the HSM hardware security module, which is also responsible for encryption, decryption, signature, verification and other related cryptographic operations.

The integrated product, which integrates certificate service and key service, can establish a complete CA system and key system through simple visual operation, and manage them in their whole life cycle.

The certificate service supports RSA2048, RSA4096, ECC256, ECC384 and other international key algorithms. It conforms to the international standard of PKI/CA, and supports national secret algorithms, including SM2, SM3 algorithms.
The key service supports AES_256, RSA_2048, RSA_3072, RSA_4096, EC_P256, EC_P384 and other international algorithms, and supports national secret algorithms, including: SM2, SM4 algorithms.

Certificate hosting: You can upload your local certificate to the certificate service to realize the unified management of certificates for users.
Key escrow: For symmetric keys, it allows you to use your own key material for sensitive data encryption and decryption services.

Certificate integration with cloud services: Deeply integrated with the proprietary load balancing service, it supports the selection of available certificates when the load balancing listener uses the HTTPS service, providing a unified interactive experience.
Key integration with cloud services: can be integrated with IAM, computing services, mirror services and other services, you can manage the key through the key service, you can also complete the encryption of local data through the key management API.

Private certificate services avoid the high cost of commercial certificates, especially during development and testing, using free certificates to test the functionality of commercial certificates can significantly reduce IT costs.
Key services provide unified key management policies and encryption apis for cloud services to use, and users do not need to build their own cryptographic infrastructure.

The keys of the key service are generated and stored by hardware encryption machines certified by the National Cryptography Administration to perform cryptographic operations, so as to ensure the security and compliance requirements of the keys.
Private CA services can issue client and server certificates, provide end-to-end encryption, and meet the needs of clients for security scenarios.

Establishes a unified enterprise certificate management system, realizes the whole life cycle management of certificates, integrates continuous monitoring and automatic management capabilities, and prevents the risk caused by poor certificate management. Certificates are used for application identity authentication and data encryption and decryption within an enterprise.

Client certificate is a digital certificate used to prove the identity of the client user, compared with the server, the user can prove his real identity when communicating with the server. It is suitable for all kinds of internal systems, network applications and network resources. Client certificate is a more secure form of digital identity authentication. Client certificate is used to securely access the system in the form of usernames and passwords.

VPN Server uses client certificate authentication mechanism instead of the traditional form of user name and password to improve VPN security and protect the internal system of the organization.

Key services use cryptographic algorithms and cryptographic devices approved by the National Cryptography Administration to easily create and control keys for encrypted data, are integrated with multiple cloud services to help you protect the confidentiality and integrity of data from these services.