
The container cluster lifecycle is automatically managed, and you only need to provide a packaged container image to run containers.

The security sandbox container technology is used to provide virtual machine level security and resource isolation capabilities. The container runtime environment is deeply optimized to provide faster startup speed than virtual machines.

It adopts consistent quota management and common network with Kubernetes container services to ensure business interoperability.
Based on the mature lightweight virtualization technology, the secure container runtime and SDN network services provide strong untrusted application isolation, fault isolation, performance isolation and multi-tenant application network isolation capabilities.
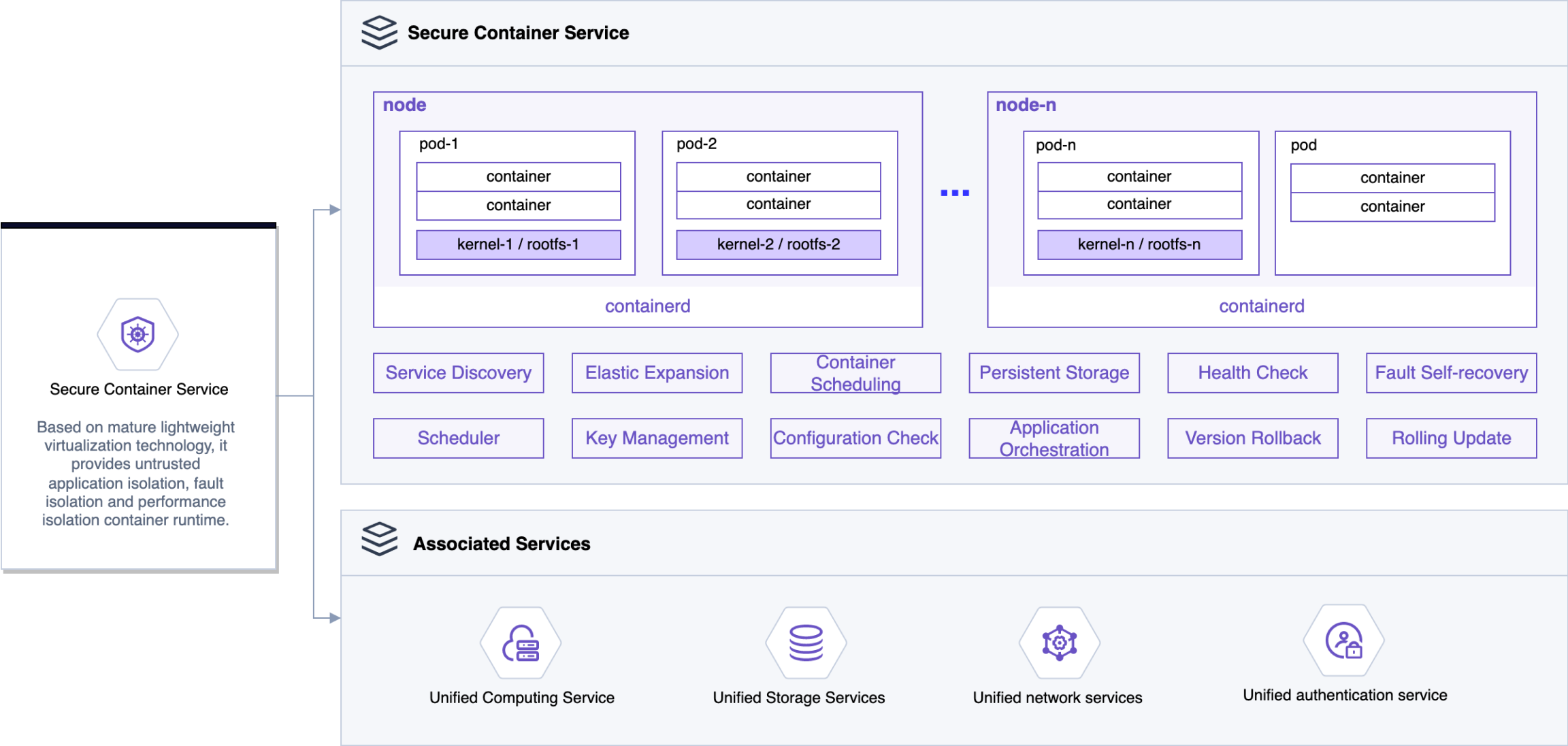

Based on the secure container runtime, it provides strong ability of untrusted application isolation and fault isolation.

The secure container can communicate with computing, storage, network and other resources in the inner network, which can allocate virtual network card, public network IP, load balancing and other resources for the container. At the same time, it also facilitates the network communication between traditional cloud host applications and container applications.

It has the same user experience as ordinary containers in terms of network, logging, monitoring, storage and so on. It has the characteristics of extreme start, excellent compatibility and stability.

Based on SDN network services, the multi-tenant application network isolation capability is added to the security container runtime.

In order to prevent the misoperation of resources, the operation ability of resources and the authorization management service of cloud platform are combined to achieve integration.

In order to prevent the abuse of resources, the quota management ability of resources and the quota management of cloud platform are combined for integrated management.
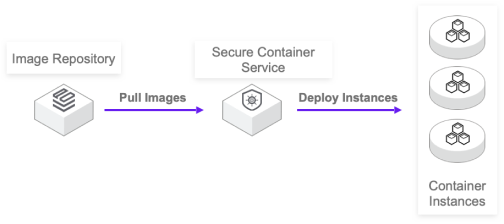
Although the traditional virtual machine deployment application has high security, it cannot enjoy the technical bonus brought by image and container, and the traditional virtual machine has large loss overhead, delivery efficiency of minutes, it is difficult to get rid of the virtual machine image, and the network self-construction and delivery are not unified. In order to solve the above pain points, the security container can start within seconds through the streamlined virtual machine. Reuse a variety of resources on the container management platform, including CNI, CSI and other general-purpose network, storage solutions.
Ordinary containers are mixed with applications of different businesses and tenants on the same node, but they all share the same kernel. When a vulnerability occurs in the kernel or runtime, malicious code will escape and have an irreversible impact on the host machine, or even cause system paralysis.
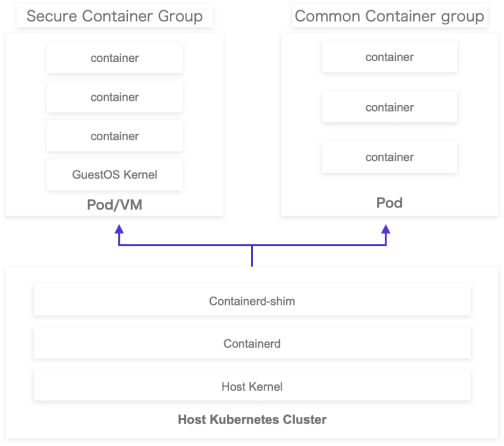
Secure container instance provides kernel-level process isolation mechanism, which naturally meets the requirement of container exclusive kernel.